Convert DKey Token to Standard TOTP (Time-based One-Time Password)
What is TOTP?
TOTP, short for Time-based One-Time Password, is a form of 2FA (two-factor authentication) that calculates a one-time password based on a pre-shared key and the current time. It generates dynamic 6-digit or 8-digit codes from a fixed secret. Both the user and the server hold the same secret, ideally only shared between them. This secret is a string of binary data that is base32 encoded for easier transmission, with the last = removed.
Background
Typically, an IT department at a university offers VPN services. Students only need to download the Cisco AnyConnect app, enter their username/password, and click “Connect” to access the school’s local area network from home or off-campus. This allows access to services that are restricted to on-campus use, such as CNKI or IEEE-Xplore. Two-step verification is essential to prevent unauthorized access to the school’s internal network if a student’s account credentials are leaked.
Our school uses the Dkey Token, but some students often face issues like accidentally uninstalling the app, data corruption on their phones, or changing devices. The standard procedure is to submit a ticket or workflow to ITSC to unlink and reactivate 2FA on the campus network. However, the ITSC takes a long time to process these requests, making it difficult for students to perform actions on their phones. Many don’t even know what 2FA is.
I discovered a way to export the seed from the Dkey Token and import it into other 2FA applications, such as One Time Password, CanoKeys, Microsoft Authenticator, etc.
Getting Started
Our ITSC provides instructions for students to install the Dkey Token themselves, along with a QR code for scanning.
The QR code contains (details have been anonymized):
http://mtc.ndkey.com/mtc/appDownload/index.html#eyJ2ZXJzaW9uIjoxLCJzZXJ2aWNlSWQiOiJTTjExNDUxNDE5MTk4MSIsImNvbXBhbnlOYW1lIjoi5YWs5Y+45ZCN56ewIiwiYWN0aXZhdGlvbk1ldGhvZCI6Miwic2VydmljZUFkZHJlc3MiOiIxMS40LjUuMTQiLCJzZXJ2aWNlUG9ydCI6NDQzLCJ0ZW5hbnRJZCI6ImRlYWRiZWVmLWNhZmUtYmFiZS1mYWNlLWRlYWRiZWVmY2FmZSJ9
(This step seems ineffective.) We decode it using echo <base64data> | base64 -d and get (details have been anonymized):
{
"version": 1,
"serviceId": "SN114514191981",
"companyName": "Company Name",
"activationMethod": 2,
"serviceAddress": "11.4.5.14",
"servicePort": 443,
"tenantId": "deadbeef-cafe-babe-face-deadbeefcafe"
}
Scanning the QR code with the Dkey Token, I captured the packets during the activation process using packet capture software. (For reference, content is somewhat dated.)
{
"requestId": null,
"success": true,
"errorCode": 0,
"errorId": null,
"data": "{\"serial\":\"114514\",\"crypto\":1,\"seed\":\"beefbeefbeefbeefbeefbeefbeefbeefbeefbeef\",\"timeStep\":60,\"passwordLength\":6}",
"message": null
}
Now we have the seed. Note that timeStep and passwordLength indicate the validity period of the one-time password and the length of the password. The seed is in hexString format (a string of hexadecimal characters) and needs to be base32 encoded for use.
Obtaining the Base32 Encoded Secret
Using this website: https://emn178.github.io/online-tools/base32_encode.html
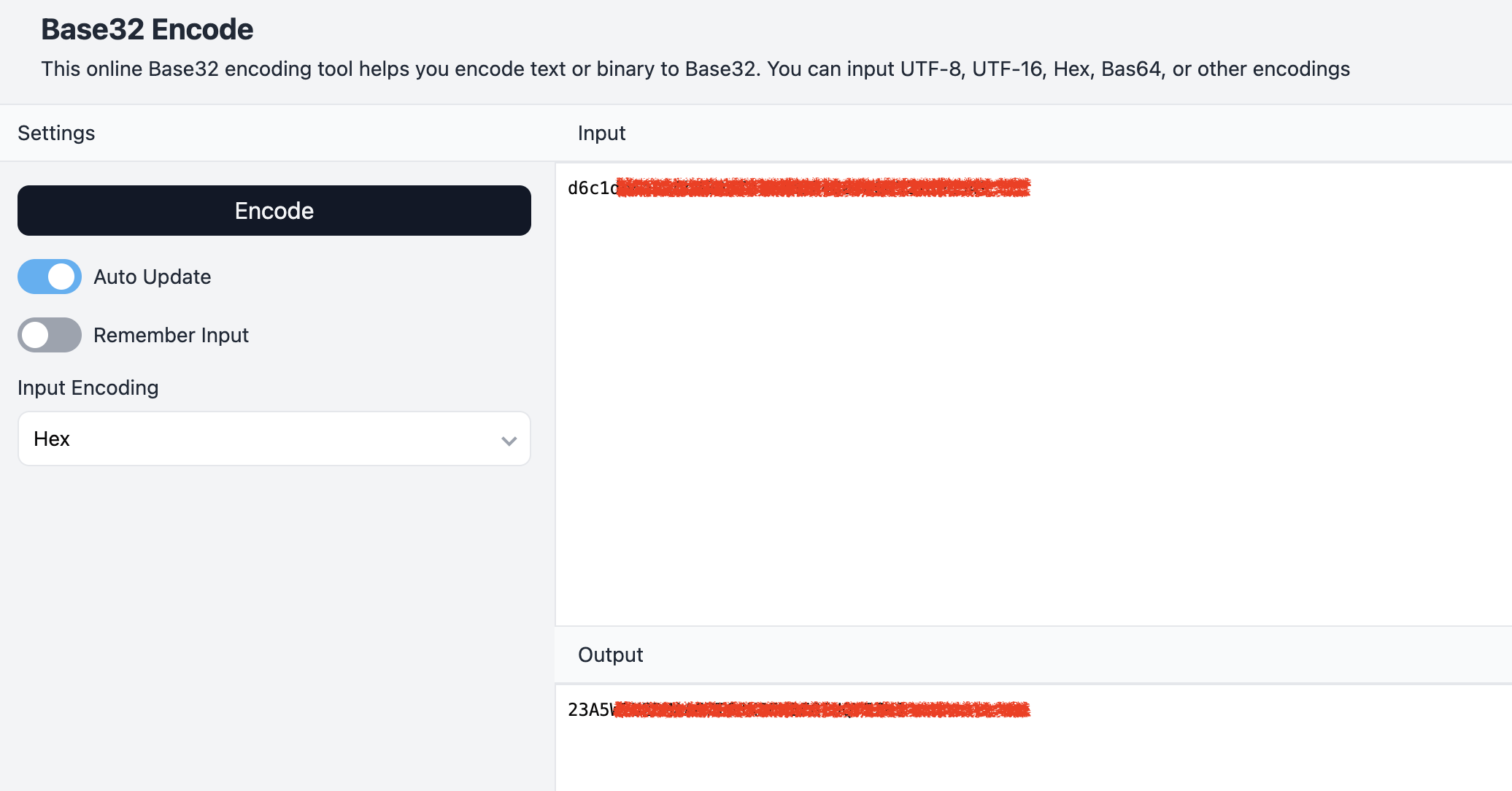
We can now obtain the base32 encoded secret.
Importing the Secret into Third-Party Applications
Now we can use it to generate TOTP. We can import and activate TOTP in apps like HE Network Tools, CanoKeys, Microsoft Authenticator, etc.
Enjoy